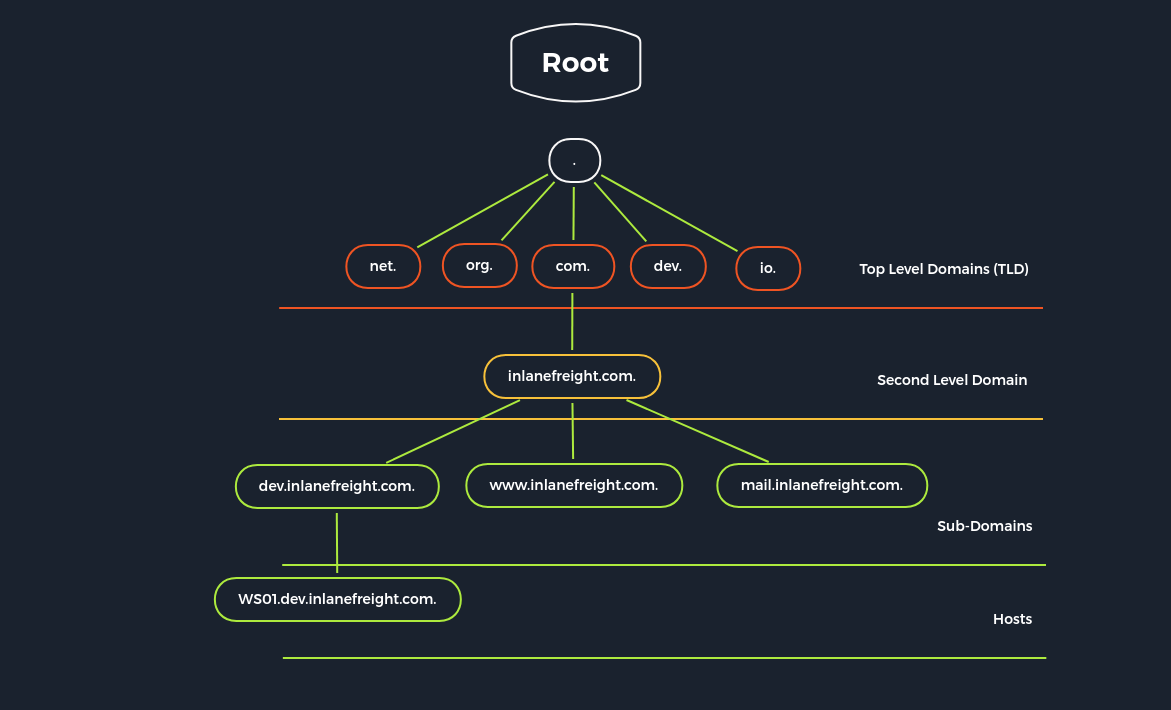
DNS
| Server Type | Description |
|---|---|
DNS Root Server |
The root servers of the DNS are responsible for the top-level domains (TLD). As the last instance, they are only requested if the name server does not respond. Thus, a root server is a central interface between users and content on the Internet, as it links domain and IP address. The Internet Corporation for Assigned Names and Numbers (ICANN) coordinates the work of the root name servers. There are 13 such root servers around the globe. |
Authoritative Nameserver |
Authoritative name servers hold authority for a particular zone. They only answer queries from their area of responsibility, and their information is binding. If an authoritative name server cannot answer a client's query, the root name server takes over at that point. |
Non-authoritative Nameserver |
Non-authoritative name servers are not responsible for a particular DNS zone. Instead, they collect information on specific DNS zones themselves, which is done using recursive or iterative DNS querying. |
Caching DNS Server |
Caching DNS servers cache information from other name servers for a specified period. The authoritative name server determines the duration of this storage. |
Forwarding Server |
Forwarding servers perform only one function: they forward DNS queries to another DNS server. |
Resolver |
Resolvers are not authoritative DNS servers but perform name resolution locally in the computer or router. |
Footprinting the Service
Query DNS server if other name servers are known
neutron@kali[/kali]$ dig ns LEGALCORP.xyz @10.129.14.128
; <<>> DiG 9.16.1-Ubuntu <<>> ns LEGALCORP.xyz @10.129.14.128
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 45010
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
; COOKIE: ce4d8681b32abaea0100000061475f73842c401c391690c7 (good)
;; QUESTION SECTION:
;LEGALCORP.xyz. IN NS
;; ANSWER SECTION:
LEGALCORP.xyz. 604800 IN NS ns.LEGALCORP.xyz.
;; ADDITIONAL SECTION:
ns.LEGALCORP.xyz. 604800 IN A 10.129.34.136
;; Query time: 0 msec
;; SERVER: 10.129.14.128#53(10.129.14.128)
;; WHEN: So Sep 19 18:04:03 CEST 2021
;; MSG SIZE rcvd: 107
use any to view all available records
neutron@kali[/kali]$ dig any LEGALCORP.xyz @10.129.14.128
; <<>> DiG 9.16.1-Ubuntu <<>> any LEGALCORP.xyz @10.129.14.128
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 7649
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 5, AUTHORITY: 0, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
; COOKIE: 064b7e1f091b95120100000061476865a6026d01f87d10ca (good)
;; QUESTION SECTION:
;LEGALCORP.xyz. IN ANY
;; ANSWER SECTION:
LEGALCORP.xyz. 604800 IN TXT "v=spf1 include:mailgun.org include:_spf.google.com include:spf.protection.outlook.com include:_spf.atlassian.net ip4:10.129.124.8 ip4:10.129.127.2 ip4:10.129.42.106 ~all"
LEGALCORP.xyz. 604800 IN TXT "atlassian-domain-verification=t1rKCy68JFszSdCKVpw64A1QksWdXuYFUeSXKU"
LEGALCORP.xyz. 604800 IN TXT "MS=ms97310371"
LEGALCORP.xyz. 604800 IN SOA LEGALCORP.xyz. root.LEGALCORP.xyz. 2 604800 86400 2419200 604800
LEGALCORP.xyz. 604800 IN NS ns.LEGALCORP.xyz.
;; ADDITIONAL SECTION:
ns.LEGALCORP.xyz. 604800 IN A 10.129.34.136
;; Query time: 0 msec
;; SERVER: 10.129.14.128#53(10.129.14.128)
;; WHEN: So Sep 19 18:42:13 CEST 2021
;; MSG SIZE rcvd: 437
DIG - AXFR Zone Transfer
neutron@kali[/kali]$ dig axfr LEGALCORP.xyz @10.129.14.128
; <<>> DiG 9.16.1-Ubuntu <<>> axfr LEGALCORP.xyz @10.129.14.128
;; global options: +cmd
LEGALCORP.xyz. 604800 IN SOA LEGALCORP.xyz. root.LEGALCORP.xyz. 2 604800 86400 2419200 604800
LEGALCORP.xyz. 604800 IN TXT "MS=ms97310371"
LEGALCORP.xyz. 604800 IN TXT "atlassian-domain-verification=t1rKCy68JFszSdCKVpw64A1QksWdXuYFUeSXKU"
LEGALCORP.xyz. 604800 IN TXT "v=spf1 include:mailgun.org include:_spf.google.com include:spf.protection.outlook.com include:_spf.atlassian.net ip4:10.129.124.8 ip4:10.129.127.2 ip4:10.129.42.106 ~all"
LEGALCORP.xyz. 604800 IN NS ns.LEGALCORP.xyz.
app.LEGALCORP.xyz. 604800 IN A 10.129.18.15
internal.LEGALCORP.xyz. 604800 IN A 10.129.1.6
mail1.LEGALCORP.xyz. 604800 IN A 10.129.18.201
ns.LEGALCORP.xyz. 604800 IN A 10.129.34.136
LEGALCORP.xyz. 604800 IN SOA LEGALCORP.xyz. root.LEGALCORP.xyz. 2 604800 86400 2419200 604800
;; Query time: 4 msec
;; SERVER: 10.129.14.128#53(10.129.14.128)
;; WHEN: So Sep 19 18:51:19 CEST 2021
;; XFR size: 9 records (messages 1, bytes 520)
DIG - AXFR Zone Transfer - Internal
neutron@kali[/kali]$ dig axfr internal.LEGALCORP.xyz @10.129.14.128
; <<>> DiG 9.16.1-Ubuntu <<>> axfr internal.LEGALCORP.xyz @10.129.14.128
;; global options: +cmd
internal.LEGALCORP.xyz. 604800 IN SOA LEGALCORP.xyz. root.LEGALCORP.xyz. 2 604800 86400 2419200 604800
internal.LEGALCORP.xyz. 604800 IN TXT "MS=ms97310371"
internal.LEGALCORP.xyz. 604800 IN TXT "atlassian-domain-verification=t1rKCy68JFszSdCKVpw64A1QksWdXuYFUeSXKU"
internal.LEGALCORP.xyz. 604800 IN TXT "v=spf1 include:mailgun.org include:_spf.google.com include:spf.protection.outlook.com include:_spf.atlassian.net ip4:10.129.124.8 ip4:10.129.127.2 ip4:10.129.42.106 ~all"
internal.LEGALCORP.xyz. 604800 IN NS ns.LEGALCORP.xyz.
dc1.internal.LEGALCORP.xyz. 604800 IN A 10.129.34.16
dc2.internal.LEGALCORP.xyz. 604800 IN A 10.129.34.11
mail1.internal.LEGALCORP.xyz. 604800 IN A 10.129.18.200
ns.internal.LEGALCORP.xyz. 604800 IN A 10.129.34.136
vpn.internal.LEGALCORP.xyz. 604800 IN A 10.129.1.6
ws1.internal.LEGALCORP.xyz. 604800 IN A 10.129.1.34
ws2.internal.LEGALCORP.xyz. 604800 IN A 10.129.1.35
wsus.internal.LEGALCORP.xyz. 604800 IN A 10.129.18.2
internal.LEGALCORP.xyz. 604800 IN SOA LEGALCORP.xyz. root.LEGALCORP.xyz. 2 604800 86400 2419200 604800
;; Query time: 0 msec
;; SERVER: 10.129.14.128#53(10.129.14.128)
;; WHEN: So Sep 19 18:53:11 CEST 2021
;; XFR size: 15 records (messages 1, bytes 664)
The individual A records with the hostnames can also be found out with the help of a brute-force attack.
neutron@kali[/kali]$ for sub in $(cat /opt/useful/SecLists/Discovery/DNS/subdomains-top1million-110000.txt);do dig $sub.LEGALCORP.xyz @10.129.14.128 | grep -v ';\|SOA' | sed -r '/^\s*$/d' | grep $sub | tee -a subdomains.txt;done
ns.LEGALCORP.xyz. 604800 IN A 10.129.34.136
mail1.LEGALCORP.xyz. 604800 IN A 10.129.18.201
app.LEGALCORP.xyz. 604800 IN A 10.129.18.15
Using DNSenum
neutron@kali[/kali]$ dnsenum --dnsserver 10.129.14.128 --enum -p 0 -s 0 -o subdomains.txt -f /opt/useful/SecLists/Discovery/DNS/subdomains-top1million-110000.txt LEGALCORP.xyz
dnsenum VERSION:1.2.6
----- LEGALCORP.xyz -----
Host's addresses:
__________________
Name Servers:
______________
ns.LEGALCORP.xyz. 604800 IN A 10.129.34.136
Mail (MX) Servers:
___________________
Trying Zone Transfers and getting Bind Versions:
_________________________________________________
unresolvable name: ns.LEGALCORP.xyz at /usr/bin/dnsenum line 900 thread 1.
Trying Zone Transfer for LEGALCORP.xyz on ns.LEGALCORP.xyz ...
AXFR record query failed: no nameservers
Brute forcing with /home/cryanight/Pentesting/SecLists/Discovery/DNS/subdomains-top1million-110000.txt:
_______________________________________________________________________________________________________
ns.LEGALCORP.xyz. 604800 IN A 10.129.34.136
mail1.LEGALCORP.xyz. 604800 IN A 10.129.18.201
app.LEGALCORP.xyz. 604800 IN A 10.129.18.15
ns.LEGALCORP.xyz. 604800 IN A 10.129.34.136
...SNIP...
done.